Password Reset Link Doesn’t Expires On Email Change
Summary : Password
When an actor claims to have a given identity, the software does not prove or insufficiently proves that the claim is correct. This can be listed under improper authentication. Password
When any user sends the password reset link but does not use it and it remains unused in the user’s inbox,
here if in any case, the attacker gets access to the victim’s main inbox (gmail or yahoo) he/she can takeover the account on the other websites which is being used by the user with the same email.
Why does this happen?
- Websites forget to set the email expiration time.
- Websites don’t expire the old password reset link on email change
- Websites don’t expire the password reset token after being used once
How to find this vulnerability ?
- Go to your target website and send a reset link to your account
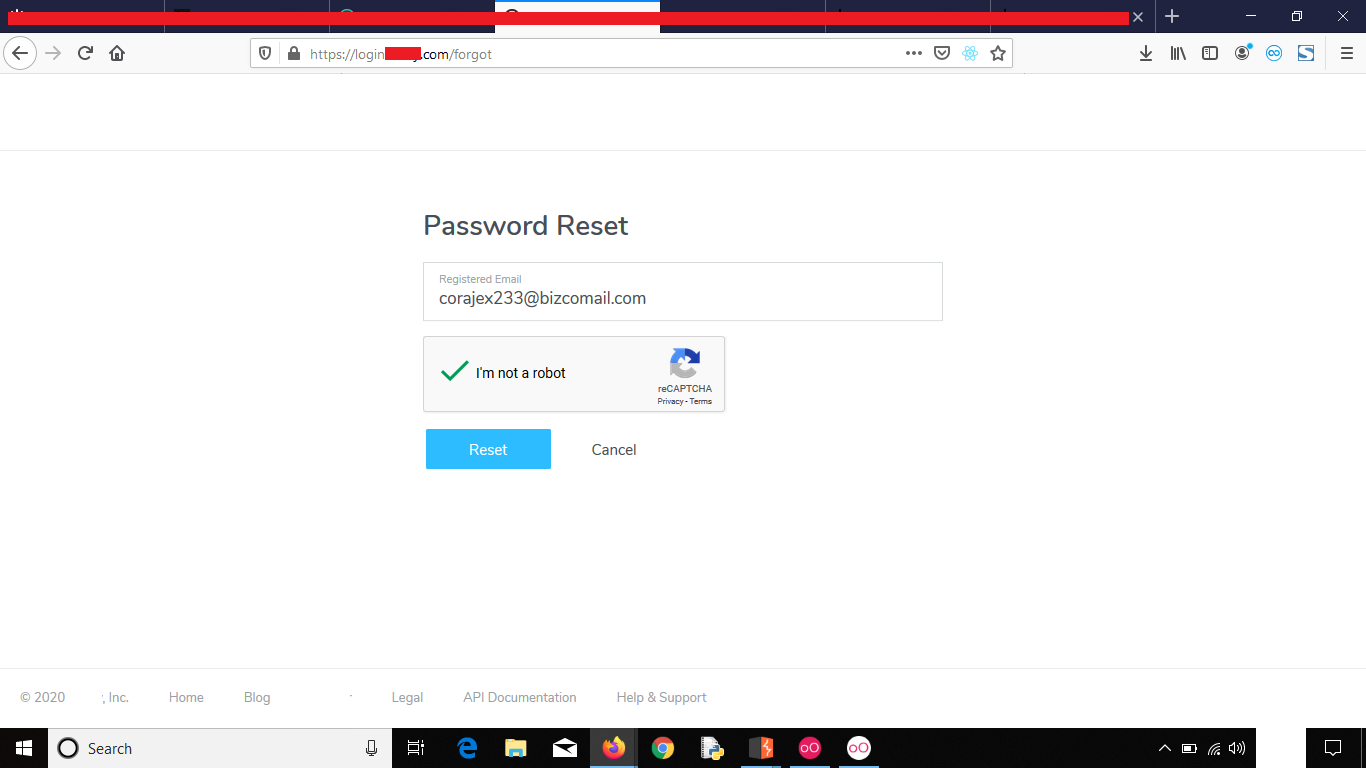
2. Now don’t use it, just login to your account and change the email Password
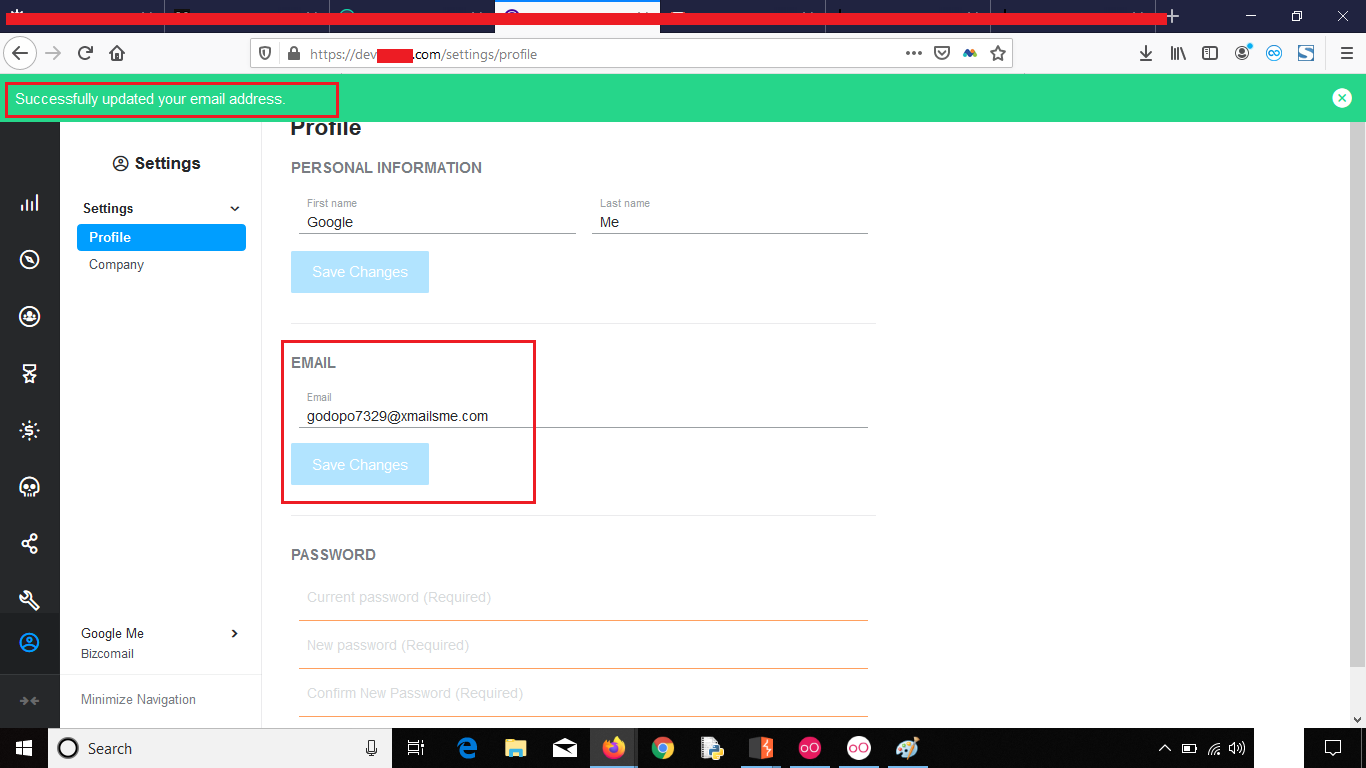
3. Now after changing the email and confirming it logout of the account and use that old password reset link to reset the password which was sent to your old email address.
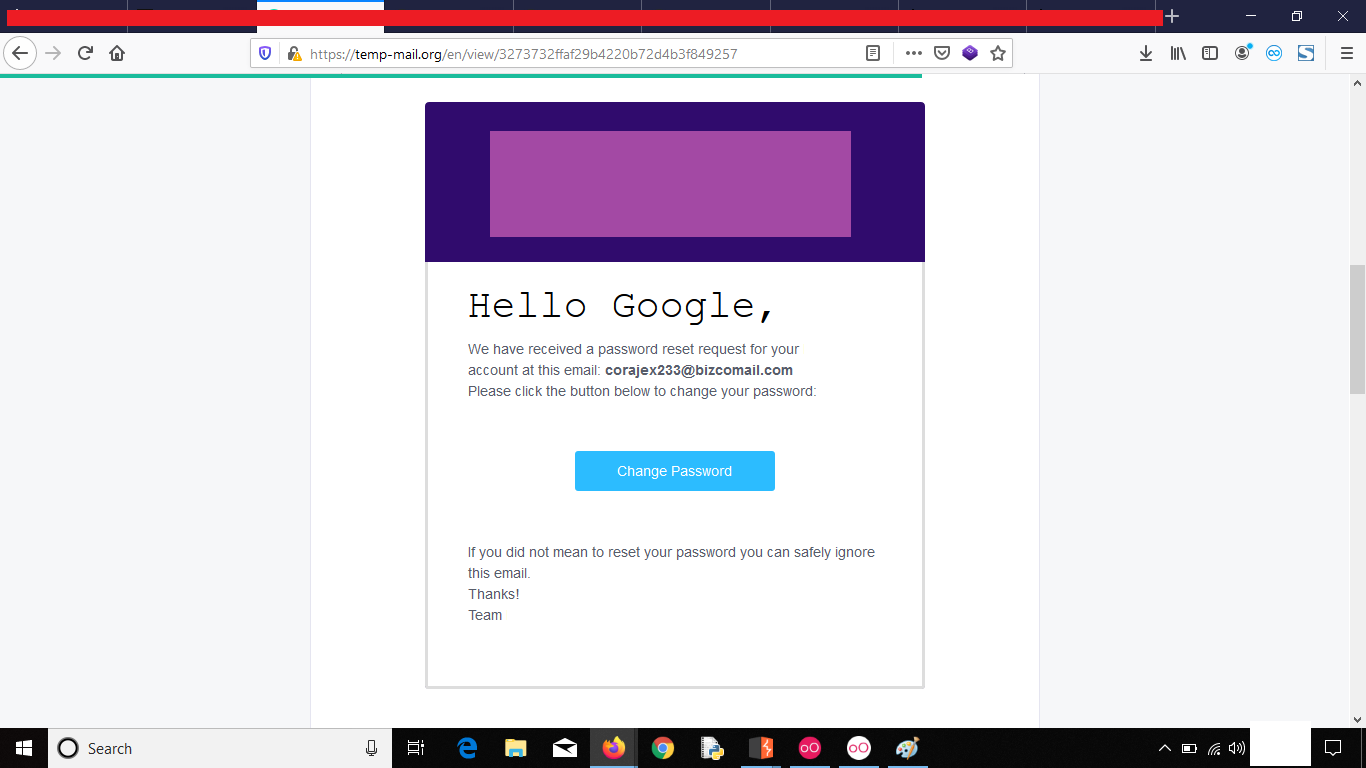
4. Now Reset the password
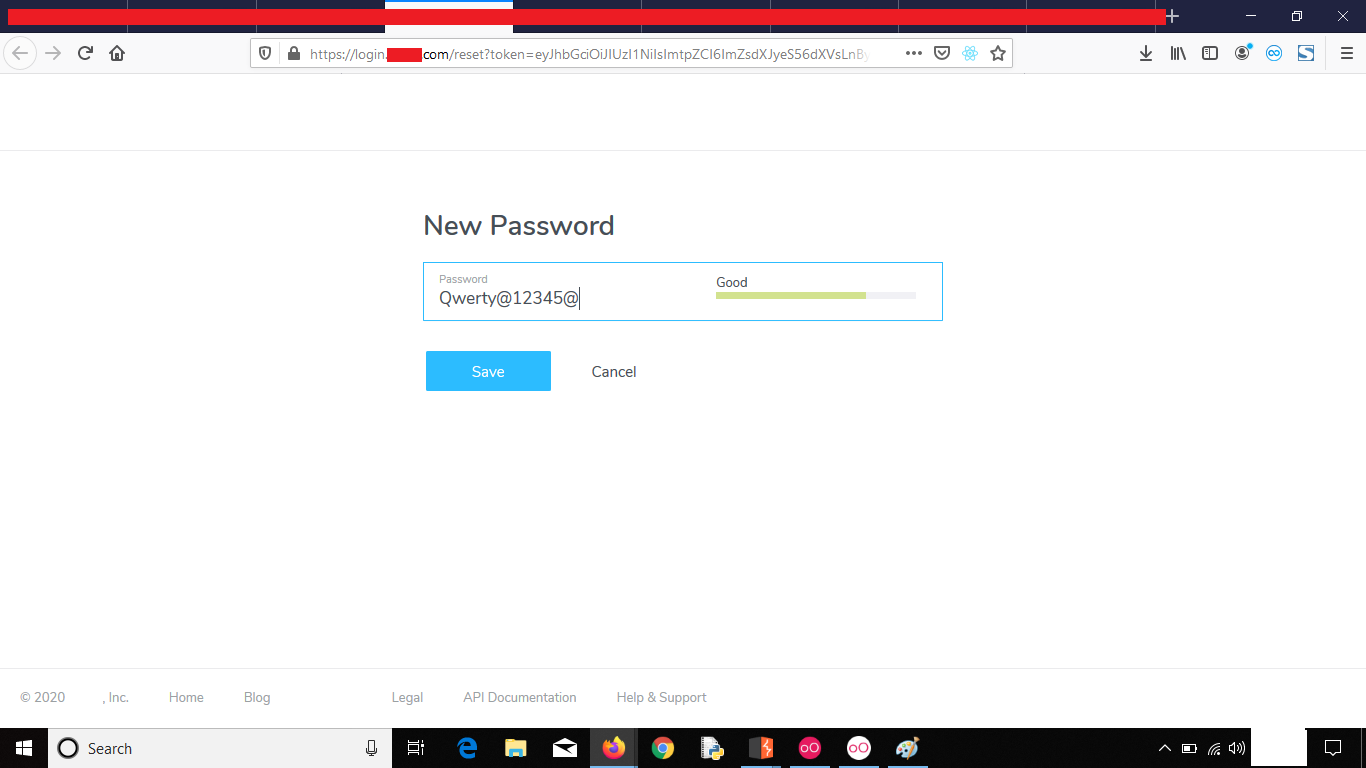
5. Log in with the changed password
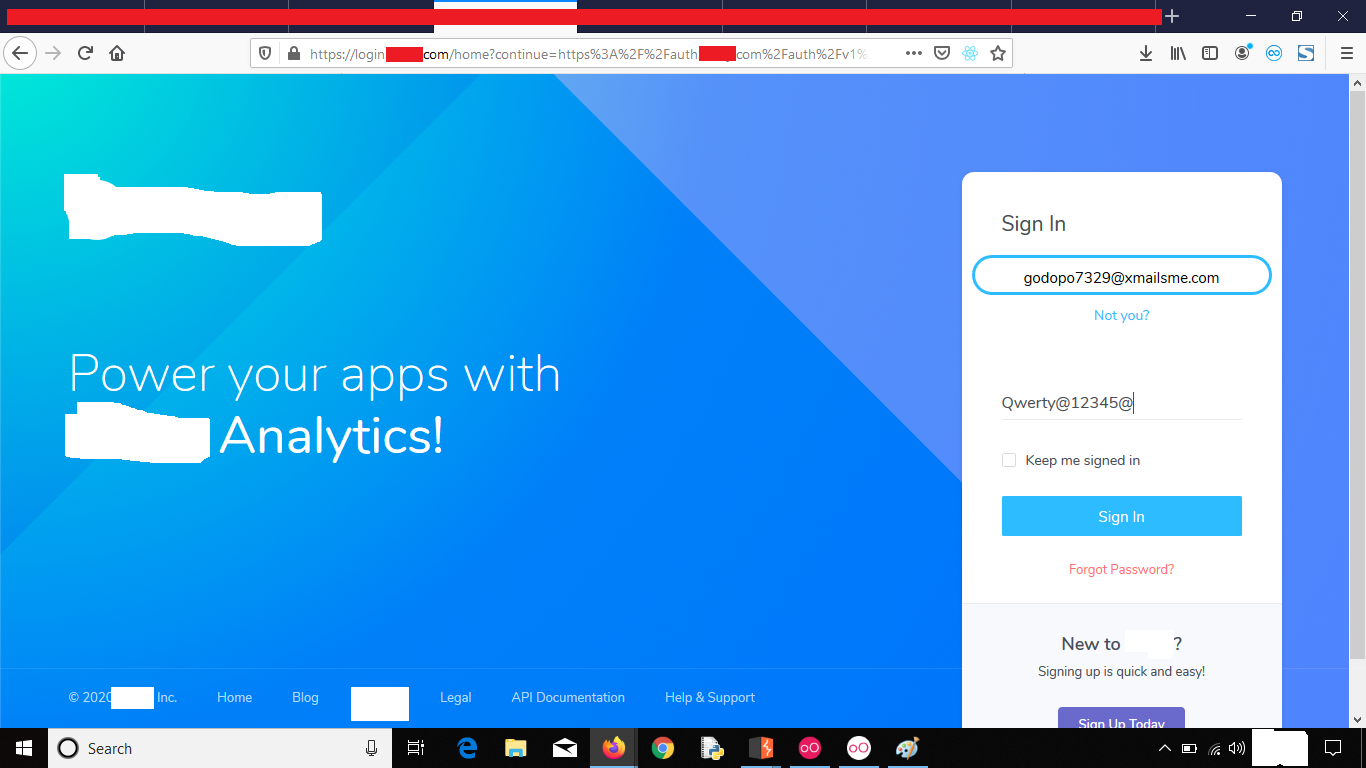
NOTE : In real case scenario it is only possible if your main account (gmail/yahoo) gets compromised. But 70 out of 100 websites accepts this risk so you can report it.
Thank You 🙂
You May also Read : http://zerothcode.com/blog/otp-bypass-developers-check/
You May also Read : http://zerothcode.com/blog/privilege-escalation-hello-admin/