OTP Bypass – Developer’s Check
Summary :
OTP is a string of characters or numbers automatically generated to be used for one single login attempt. OTP, One Time Passwords in full, can be sent to the user’s phone via SMS or Push messaging and is used to protect web-based services, private credentials and data.
I was checking for some bypasses of an OTP and I tried this thing to bypass the OTP and was successful. I call it Developer’s Check because I found it when I was reviewing the code of the application and some of the buttons. The mistake here was that the application was having the OTP check on the client side and was easily identifiable. Due to this mistake anyone can bypass the OTP very easily.
How to find this vulnerability ?
- Go to your target website


2. Here I had an option to register and they will send me an OTP for login

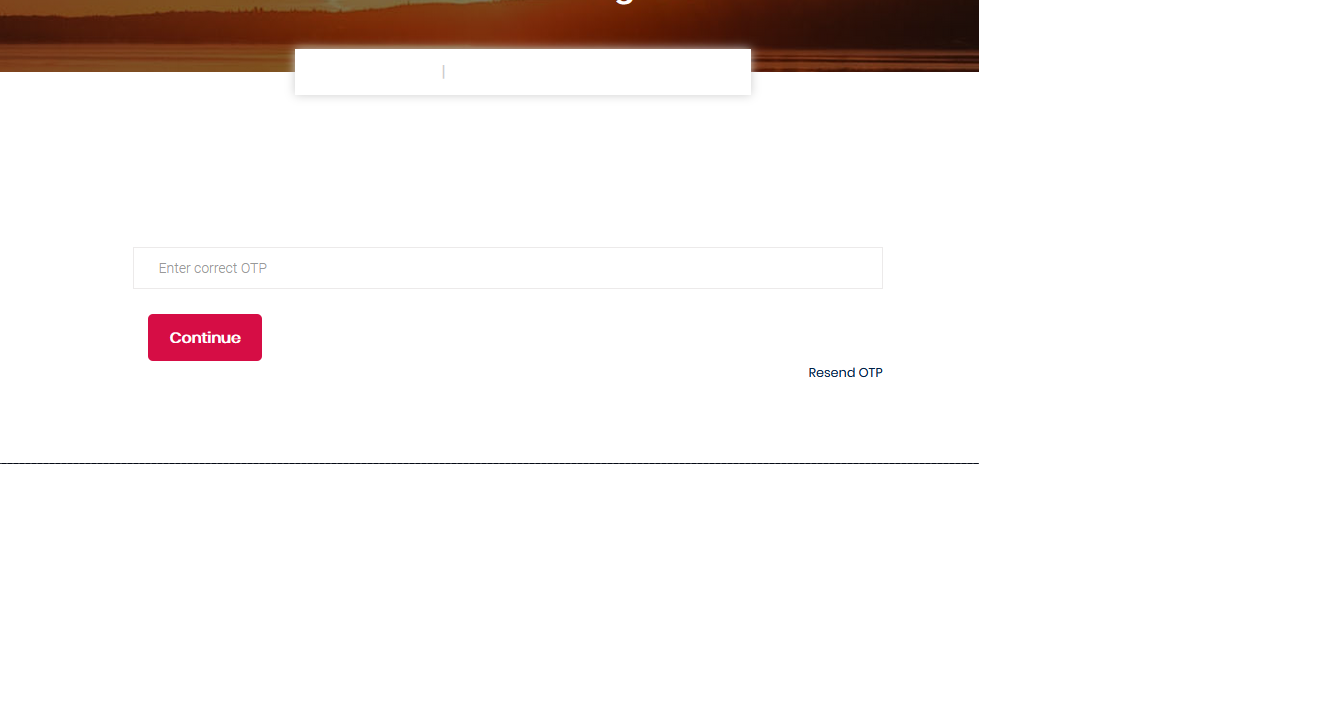
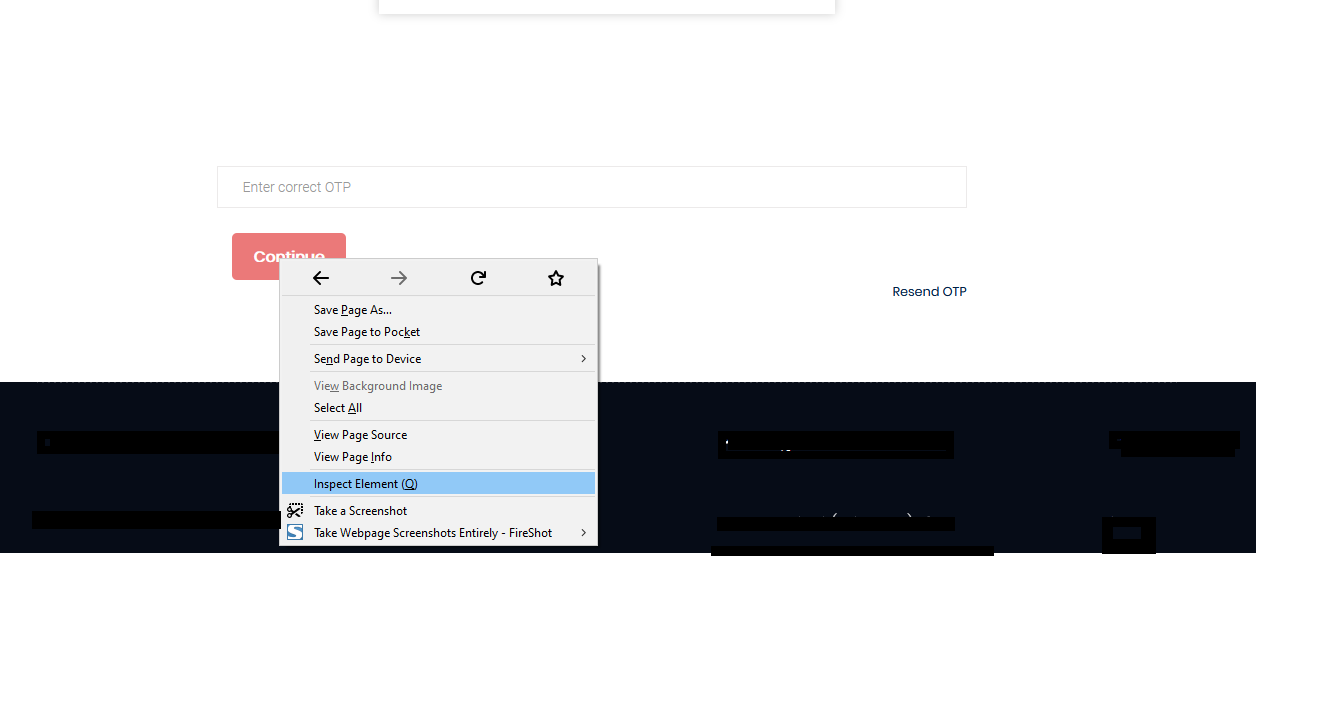
3. Right-click on the “Continue” button and click on inspect element to check for some functions that validates the OTP check
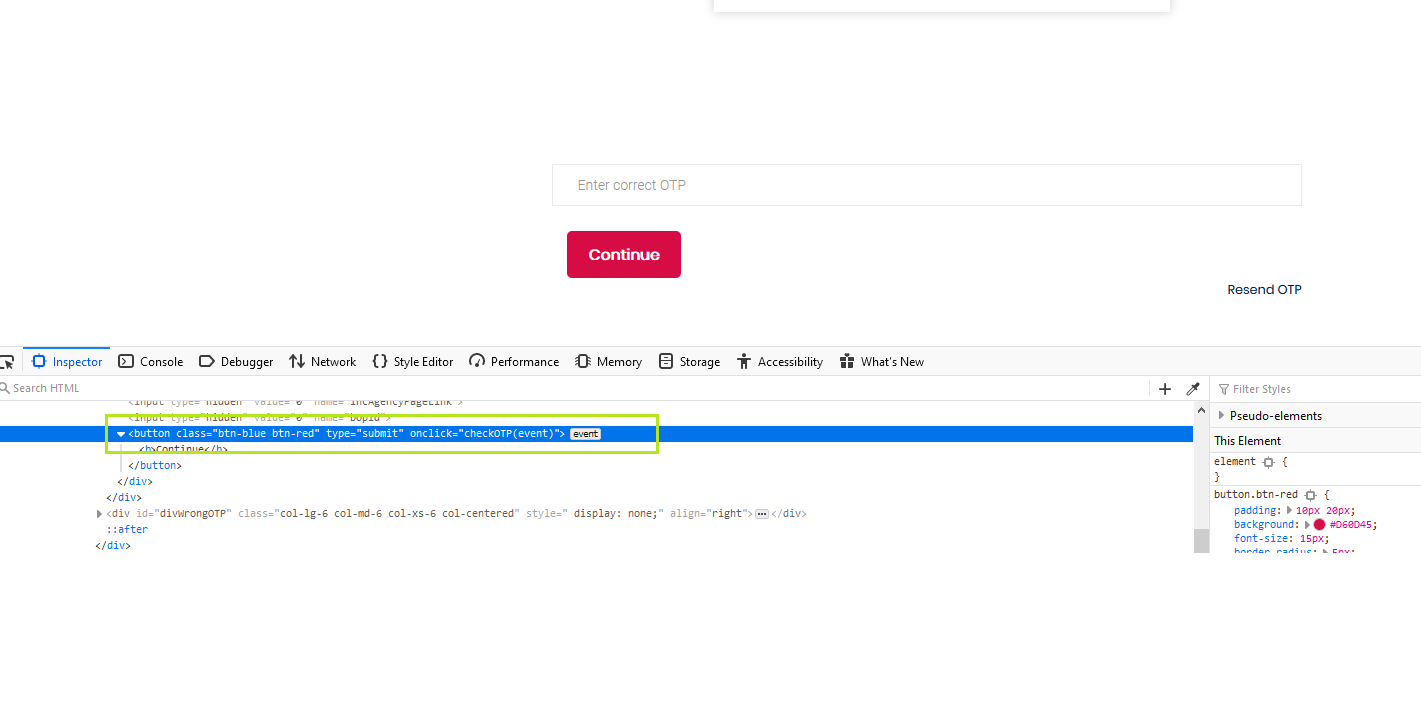
4. Here you can see in the below screenshot that their is an event called “checkOTP(event)”

5. Simply type the event in the console of the browser

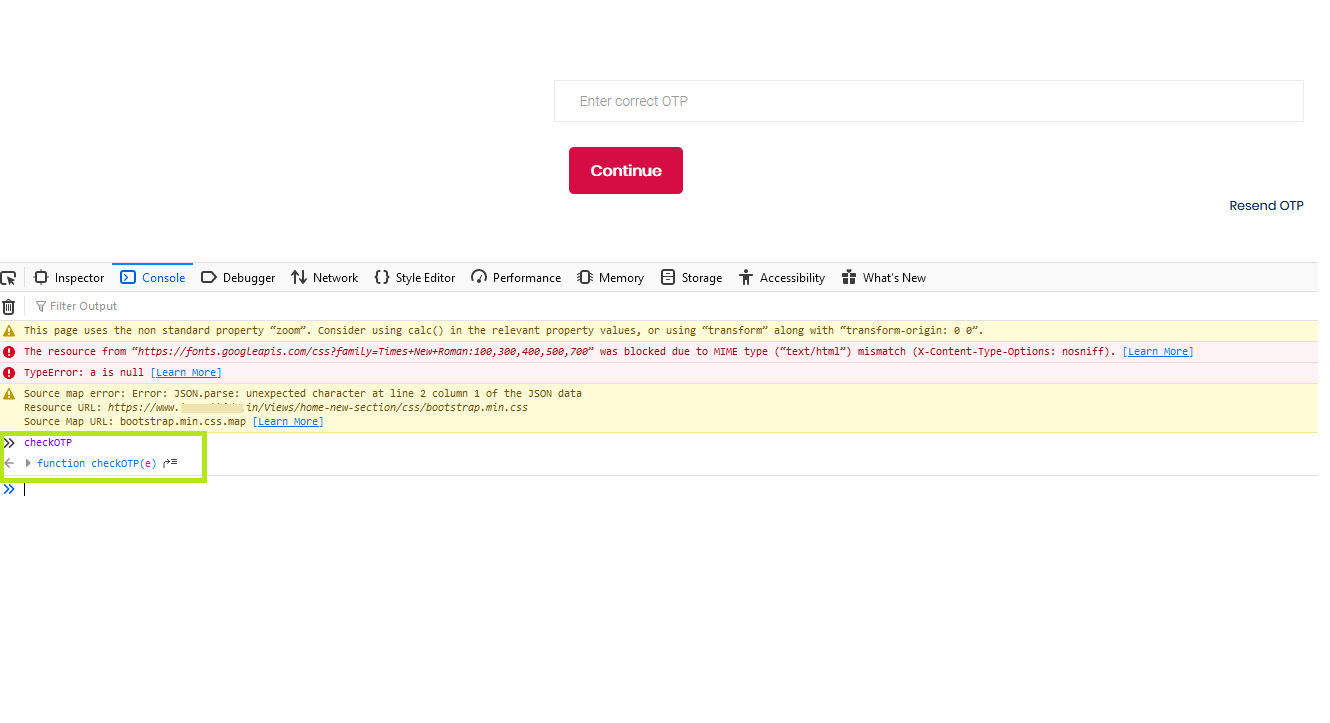
6. After clicking on the arrow it will open a file in the debugger where you will an OTP that was send to the mobile
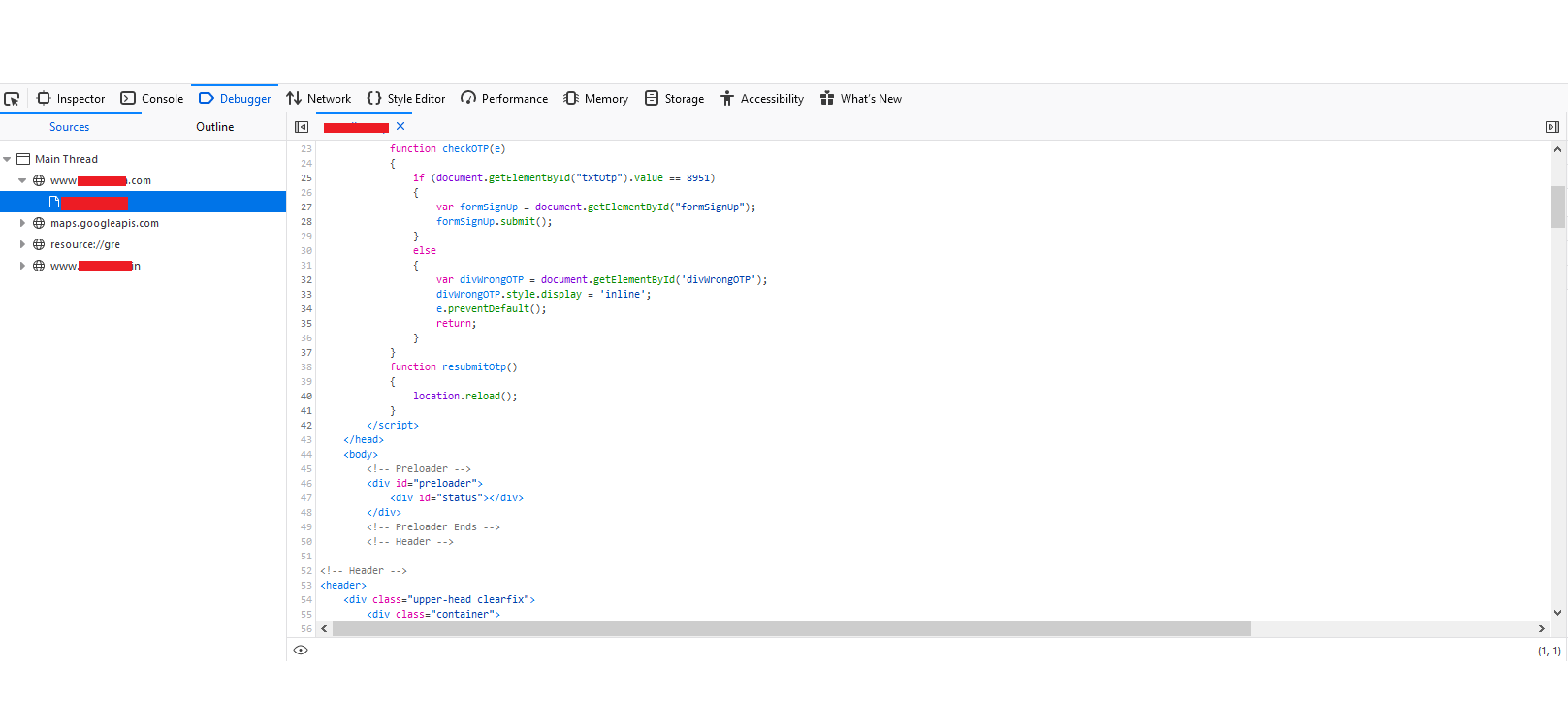
Logic Code :
<script type=’text/javascript’>
function checkOTP(e)
{
if (document.getElementById(“txtOtp”).value == 8951)
{
var formSignUp = document.getElementById(“formSignUp”);
formSignUp.submit();
}
else
{
var divWrongOTP = document.getElementById(‘divWrongOTP’);
divWrongOTP.style.display = ‘inline’;
e.preventDefault();
return;
}
}
function resubmitOtp()
{
location.reload();
}
</script>
As here you can see if “(document.getElementById(“txtOtp”).value == 8951)” which means if the OTP that you entered matches “8951” then only you will get a successful login which also means that “8951” is your OTP.
Thank You 🙂



