Google Dorks – Hacking’s New Door
Summary :
The “Google Dorks” is a technique that uses google searches to find security holes and sensitive information that is not readily available on a website. It is one of the most effective technique to find sensitive information of any website. It is also know as passive information gathering technique.
Google Dorks gives you the information which is difficult to locate through simple search queries. That description includes information that is not intended for public viewing but that has not been adequately protected.
Google Dorks can return usernames and passwords, email lists, sensitive documents, API keys, personally identifiable information, website vulnerabilities etc. That information can be used for any number of illegal activities like cyber terrorism, identity theft, cyber stalking etc.
Basics :
Google Dorks uses advanced operators in the Google search engine to locate specific strings of text within search results. Some of the popular examples for finding websites that are vulnerable to SQL injection, XSS, API keys etc. are
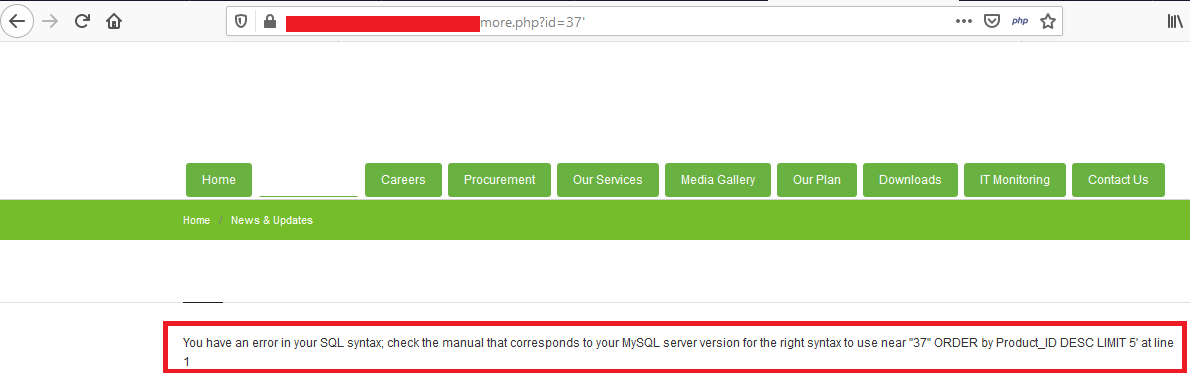
- Dork for SQL Injection – inurl: .php?id=

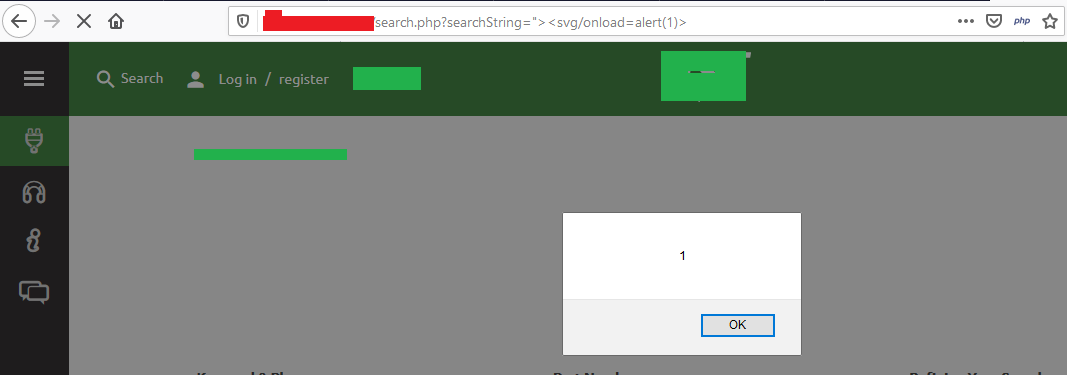
2. Dork for XSS – inurl:”.php?searchstring=”
3. Dork for API keys – intitle:”index of” api_key OR “api key” OR apiKey
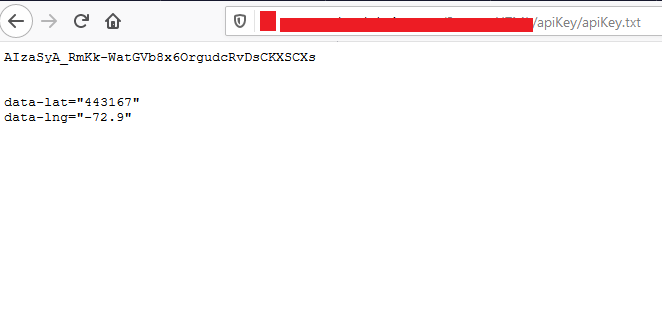
Above are the most common examples of finding some common vulnerabilities on the websites, but this aren’t the limited one.
NOTE : You can check here for more dorks : https://www.exploit-db.com/google-hacking-database
This was the basics to find the information or vulnerabilities using Google Dorks, now lets look at some of the advance and “not so popular” techniques of finding sensitive information.
Advance :
You guys are might be aware about HTTP VERBS. There are many http verbs out of which GET & POST are the most commonly used. Now we all know that the GET method is not suitable for passing sensitive information such as the username and password, because these are fully visible in the URL query string as well as potentially stored in the client browser’s memory as a visited page.
Still there are many websites that are passing sensitive information using GET method, to make it secure you can use the blocking rules. Commonly, the blocking rules could be setup easily by write some “Disallow” rules at robots.txt file.

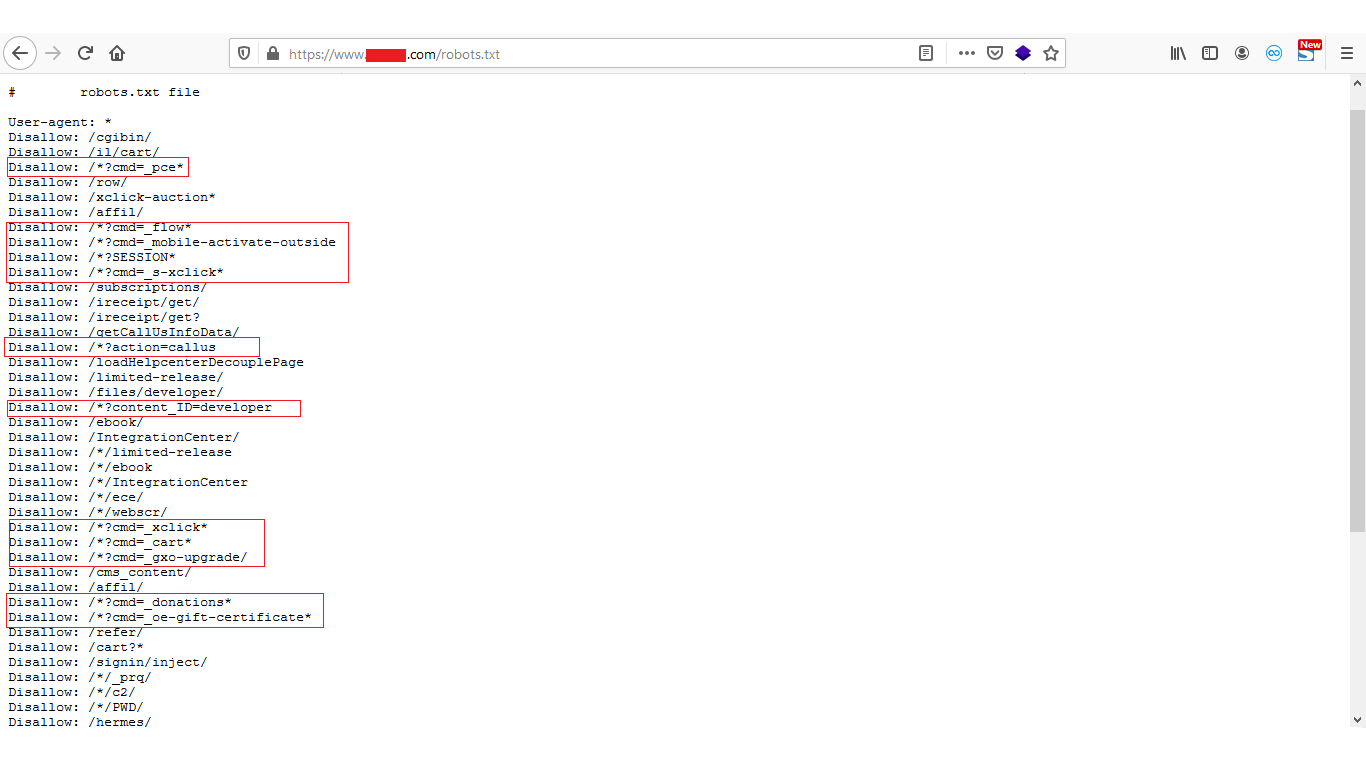
While hunting on a private program I found a request where they were using GET parameter which contained email, some key, ID, my country name etc. So I tried finding email’s of other users on the same site and I got some yahoo email ID’s
- Dork Used for yahoo : site:target.com inurl:’@yahoo.co’ (which will give me .com and .co.in) emails of yahoo

I got an excel sheet containing yahoo emails and phone numbers of the users of that site.
Now I wanted to find some more emails so I enumerated further and got emails of outlook.live and gmail.com
2. Dork Used for outlook : site:target.com inurl:’@live.com’

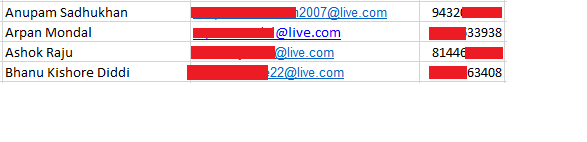
3. Dork Used for gmail : site:target.com inurl:’@gmail.com’


Some more useful dorks :
- site:<Website> inurl:<GET Parameter>
Example :
i) site:target.com inurl:api_key
ii) site:target.com inurl:email
iii) site:target.com inurl:amount
2. intitle:”index of” “/etc/mysql/”
3. site:”target.com” database.yml
4. inurl:group_concat(username, filetype:php intext:admin
5. inurl:/wwwboard/passwd.txt
6. filetype:reg reg HKEY_CLASSES_ROOT -git
7. inurl:/database* ext:sql intext:index of -site:target.com
This are some of the not so common but useful Google Dorks to find sensitive information of the website. You can also modify this dorks and you can also use more dorks with this dorks.
NOTE : You can prevent a page from appearing in Google Search by including a “noindex” meta tag in the page’s HTML code, or by returning a ‘noindex’ header in the HTTP request.
Thank You 🙂