Recon Tools For Bug Bounty
Bug Bounty Information Gathering is the most important stage of every penetration testing so that you will have a better understanding about your target to exploit vulnerabilities and information like (IP addresses, Subdomain, Open ports and etc.) but to gather the information you need proper reconnaissance tools and there are many recon tools which are available on Github but among them, I found Top 10 Recons tools which you can use to gather all of this information about your target.
Important Note Bug BountyAlways remember before scanning your target you should have proper authorization otherwise you should never use these tools to scan any other targets because while scanning the targets WAF (Web Application Firewall) monitors your network traffic and tracks your IP address and without authorization if you scan a target, you will violate the legal disclaimer of the application and you could face legal actions.
1.Nmap
Nmap is a network mapper tool and widely popular for discovering hosts and services on a network and it’s free and open-source on Github. It has many features and after scanning a network you can gather a lot of important information such as Host Discovery, Service/Version Detection and OS Detection. This tool is very useful and you can use all of this information to audit a network.
Basic Nmap command
nmap -v -A scanme.nmap.org
For more information — https://nmap.org/
2. Nikto
Nikto is widely popular for vulnerability scanner and it scans web servers to detect dangerous files, outdated server software and many more, it performs specific server type checks like (Clickjacking, MIME Type, etc.) and this tool you can scan with any web servers such as Apache, NGINX, Oracle HTTP Server, etc. This tool is quite useful to detect server misconfigurations. But the major issue of using this tool is that it’s quite easily detectable so always while scanning a network using Nikto it’s better to use a VPN (Virtual Private Network).
This tool is open-source on Github and you can install this tool with all major Operating System — (Windows, MacOSX & GNU/Linux).
Basic Nikto command
nikto -h example.com
For more information — https://cirt.net/Nikto2
3. Amass
Amass tool is developed and maintained by OWASP and this tool is used to gather information such as DNS enumeration, Subdomain name alterations, Web scraping, Certificates, Web APIs and many more. This tool is developed to help security researchers to get in-depth information about a target network
DNS: Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
Scraping: Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
Certificates: Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, GitHub, HackerTarget, IPToASN, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
Basic Amass command
amass -d example.com
For more information — https://github.com/OWASP/Amass
4. Dirsearch
Dirsearch is a free and open-source tool and widely popular for brute force directories and files in websites. This tool has many different features such as Multithreaded, Keep alive connections, multiple extensions, exporting reports in both (plain text, JSON), HTTP proxy support, User-agent randomization and many more. And you can use custom wordlist like SecList to brute-force files and directories. This tool is quite friendly and easy to use and it’s supported for three major Operating systems (Windows, MacOSX & GNU/Linux). Bug Bounty
Basic Dirsearch command
python dirsearch.py -u https://example.com -e html,php,jsp,asp,json
Dirsearch Github repo — https://github.com/maurosoria/dirsearch
5. Sublist3r
Sublist3r is widely popular to enumerate subdomains of a website and to gather subdomain it uses many popular search engines such as Google, Yahoo, Bing, Baidu and Ask and to enumerate subdomains it uses Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS. This tool is very much helpful to gather subdomains of a domain and most importantly to get better results of subdomains, subbrute was integrated with Sublist3r by using an improved wordlist. Bug Bounty
Basic Sublist3r command
python sublist3r.py -d example.com
Sublist3r Github repo — https://github.com/aboul3la/Sublist3r
6. Knockpy
Knockpy is designed to enumerate subdomain and to scan DNS zone transfer and automatically try to bypass wildcard DNS record. And most importantly it supports queries to VirusTotal subdomains and to configure in the config.json file you can set up your API_KEY. This tool most of the penetration testers and bug hunters uses to exploit Subdomain takeover vulnerability.
Basic Knockpy command
knockpy example.com
Knockpy Github repo — https://github.com/guelfoweb/knock
7. Gitrob
Gitrob tool is widely popular to find sensitive files on public Github repositories and this tool will clone user or organizations public repositories and in-depth iterate all the commit history and it matches with the potentially sensitive files such as api_key, access_token, password, database_name, etc.
To install this tool you need to have Golang set up in your local machine.
Gitrob Github repo — https://github.com/michenriksen/gitrob
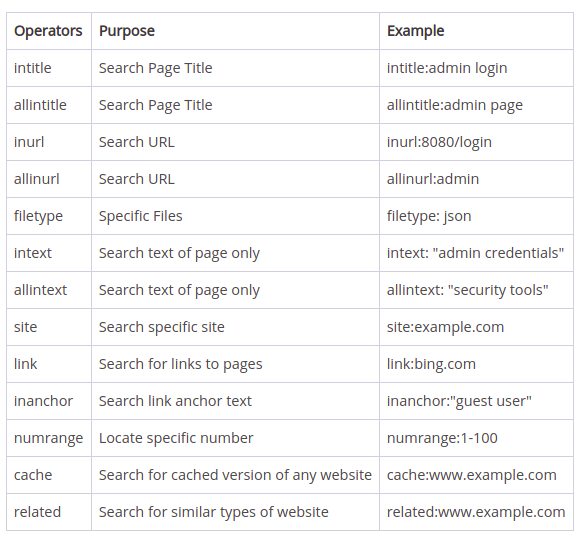
8. Google Dork
Google Dork is also named as “Google Hacking” and this is a technique to find security holes in a website through Google search. It’s so much helpful for the security researchers and using Google’s web-crawling you can gather information such as usernames, passwords and sensitive information.
Google Dork Operators
9. Shodan
Shodan is a search engine, hackers and security researchers use to find vulnerable Internet of Things devices and querying to the engine he/she can get the device IP address, web server details, banner, ISP, SSH, FTP, TELNET and many more.
For hackers, it’s a great playground to gather as much information from a target.
Basic Shodan search query
product:MongoDB
For more information — https://www.shodan.io/
10. Censys
Censys is a search engine which is pretty similar to Shodan, it allows hackers and security researchers to scans devices, hosts and gives an aggregate report on how the systems are configured (Certificates, Websites, etc.) and deployed. Censys is designed to find out poorly configured devices over the internet and due to it maintains a large amount of database it’s very much useful to gather information for a specific target.
Basic Censys search query
www.example.com
For more information — https://censys.io/
I hope you understand by now why RECON is important in Bug Bounty and I found these are the top 10 Recon tools which you can use to gather as much information for a specific target but there are also many other different tools which you can explore for information gathering, in my future tutorials I’ll demonstrate those tools.
I hope you guys like this post bye bye for now