Beware: New Android Spyware Found Posing as Telegram and Threema Apps
android mobile hacking A hacking group known for its attacks in the Middle East, at least since 2017,
has recently been found impersonating legitimate messaging apps such as Telegram and Threema to infect Android devices with a new, previously undocumented malware.
“Compared to the versions documented in 2017, Android/SpyC23. android mobile hacking
A has extended spying functionality, including reading notifications from messaging apps, call recording and screen recording, and new stealth features,
such as dismissing notifications from built-in Android security apps,” cybersecurity firm ESET said in a Wednesday analysis.
First detailed by Qihoo 360 in 2017 under the moniker Two-tailed Scorpion (aka APT-C-23 or Desert Scorpion),
the mobile malware has been deemed “surveillance ware” for its abilities to spy on the devices of targeted
individuals, android mobile hacking
exfiltrating call logs, contacts, location, messages, photos, and other sensitive documents in the process.
In 2018, Symantec discovered a newer variant of the campaign that employed a malicious media player
as a lure to grab information from the device and trick victims into installing additional malware.
Then earlier this year, Check Point Research detailed fresh signs of APT-C-23 activity
when Hamas operators posed as young teenage girls on Facebook, Instagram, and Telegram to lure Israeli soldiers into
installing malware-infected apps on their phones.
The latest version of the spyware detailed by ESET expands on these features,
including the ability to collect information from social media and messaging apps via screen recording and screenshots,
and even capture incoming and outgoing calls in WhatsApp and read the text of notifications from social media apps,
including WhatsApp, Viber, Facebook, Skype, and Messenger.
The infection begins when a victim visits a fake Android app store called “DigitalApps,”
and downloads apps such as Telegram, Threema, and message, suggesting that the group’s motivation behind impersonating messaging apps is to
“justify the various permissions requested by the malware.”
In addition to requesting invasive permissions to read notifications, turn off Google Play Protect,
and record a user’s screen under the guise of security and privacy features,
android mobile hacking
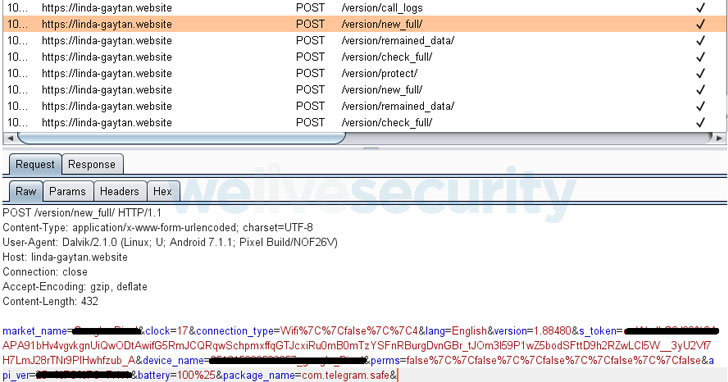
the malware communicates with its command-and-control (C2) server to register the newly infected victim and transmit the device information.
The C2 servers, which typically masquerade as websites under maintenance, are also responsible for relaying the commands to the compromised phone,
which can be used to record audio, restart Wi-Fi, uninstall any app installed on the device, among others.
What’s more, it also comes equipped with a new feature that allows it to stealthily make a call while creating a black screen overlay to mask the call activity.
“Our research shows that the APT-C-23 group is still active, enhancing its mobile toolset and running new operations. android mobile hacking
Android/SpyC32.A – the group’s newest spyware version
— features several improvements making it more dangerous to victims,” ESET said.
Apps downloaded from fraudulent third-party app stores has been a conduit for Android malware in recent years.
It’s always essential to stick to official sources to limit risk,
and scrutinize permissions requested by apps before installing them on the device. android mobile hacking
You May Also interested to read this article
http://zerothcode.com/blog/play-store-coronavirus-outbreak/
http://zerothcode.com/blog/burp-suite-monitor-endpoints/
http://zerothcode.com/blog/traxss-automated-xss-scanner/
http://zerothcode.com/blog/penta-automate-pentesting/
Have something to say about this article? Comment below or share it with us on Facebook, Twitter, or our LinkedIn Group.