Just An SMS Could Let Remote Attackers Access All Your Emails, Experts Warn
Beware! Billion of Android users can easily be tricked into changing their devices’ critical network settings with just an SMS-based phishing attack. SMS
Whenever you insert a new SIM in your phone and connects to your cellular network for the very first time, your carrier service automatically configures or sends you a message containing network-specific settings required to connect to data services.
While manually installing it on your device, have you ever noticed what configurations these messages, technically known as OMA CP messages, include?
Well, believe me, most users never bother about it if their mobile Internet services work smoothly.
But you should worry about these settings, as installing untrusted settings can put your data privacy at risk, allowing remote attackers to spy on your data communications, a team of cybersecurity researchers told The Hacker News.

Well, there’s some good news for hackers and vulnerability hunters, though terrible news for Google, Android device manufacturers, and their billions of users worldwide. SMS
The zero-day buying and selling industry has recently taken a shift towards Android operating system, offering up to $2.5 million payouts to anyone who sells ‘full chain, zero-click, with persistence’ Android zero-days. SMS
Just like other traditional markets, the zero-day market is also a game of supply, demand, and strategy, which suggests either the demand of Android zero-days has significantly increased or somehow Android OS is getting tougher to hack remotely, which is unlikely.
In it’s latest notification, Zerodium—a startup that buys zero-day exploits from hackers, and then probably sells them to law enforcement agencies and nation-sponsored spies around the world—said it’s looking for hackers who can develop full chain Android exploits.
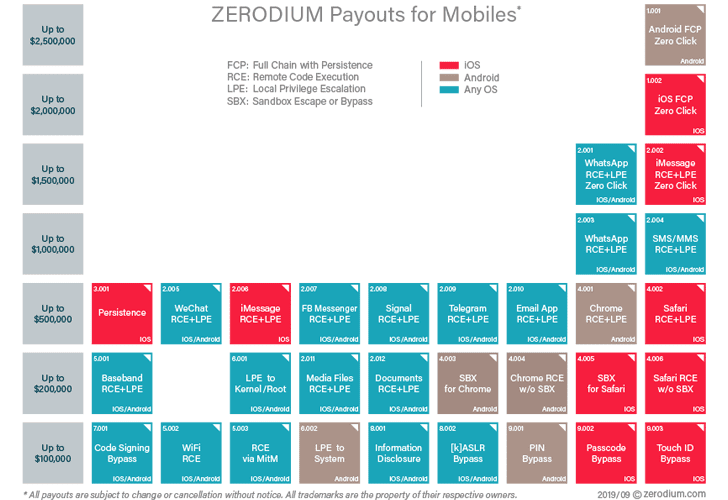
The company is ready to pay up to $2.5 million for such exploits that can be used to gain persistence access on an Android device with no indication and interaction from the target user; a straight 12x jump from its previous price tag of $200,000.
While the same type of zero-day exploits for iOS devices are worth $2 million, which is still double than what Apple has recently started offering to hackers to responsibly report severe deadly exploits, described as “a zero-click kernel code execution vulnerability that enables complete, persistent control of a device’s kernel.”
Besides Android exploits, Zerodium has also announced to offer $500,000 for submitting new persistence exploits or techniques for iOS, and increased payouts of WhatsApp and iMessage exploits.



