MobiKwik Suffers Major Breach — KYC Data of 3.5 Million Users Exposed
Popular Indian mobile payments service MobiKwik on Monday came under fire after 8.2 terabytes (TB) of data belonging to millions of its users began circulating on the dark web in the aftermath of a major data breach that came to light earlier this month.
The leaked data includes sensitive personal information such as:
- customer names,
- hashed passwords,
- email addresses,
- residential addresses,
- GPS locations,
- list of installed apps,
- partially-masked credit card numbers,
- connected bank accounts and associated account numbers,
- and even know your customer (KYC) documents of 3.5 million users.
Even worse, the leak also shows that MobiKwik does not delete the card information from its servers even after a user has removed them, in what’s likely a breach of government regulations.
New guidelines issued by India’s apex banking institution, the Reserve Bank of India, prohibit online merchants, e-commerce websites, and payment aggregators from storing card details of a customer online. The rules are set to come into effect starting July 2021.
As of July 2020, MobiKwik serves 120 million users and 3 million retailers across the country.
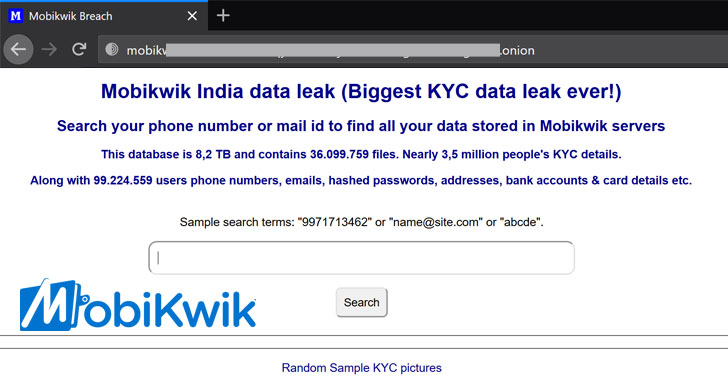
The data leak site, which is accessible via Tor browser and boasts of 36,099,759 records, came online after the digital wallet company vehemently denied the incident on March 4 following a report by an independent security researcher Rajshekhar Rajaharia.
“A media-crazed so-called security researcher has repeatedly over the last week presented concocted files wasting precious time of our organization while desperately trying to grab media attention,” MobiKwik tweeted. “We thoroughly investigated his allegations and did not find any security lapses. The various sample text files that he has been showcasing prove nothing. Anyone can create such text files to falsely harass any company.”
However, multiple users have confirmed to the contrary, finding their personal details in the “MobiKwik India data leak” site, lending credence to the breach.
“Never *ever* behave as @MobiKwik has in this thread from 25 days ago,” Troy Hunt, security researcher and creator of breach notification tool Have I Been Pwned, said in a tweet, calling out the company MobiKwik’s handling of the situation.
According to sources close to the incident,
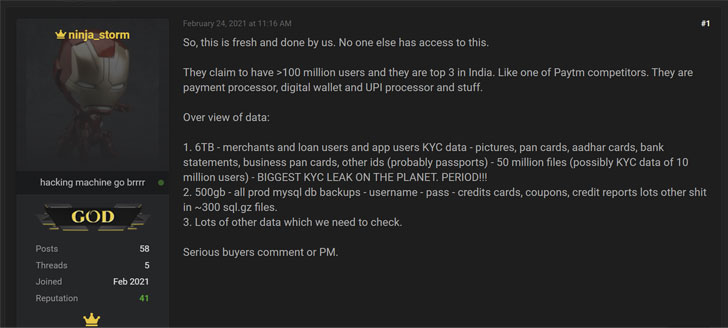
the compromise was originally advertised in a database leaking forum on February 24, with a hacker claiming access to 6TB data from an unnamed Paytm competitor.
Interestingly, it appears that after Rajaharia disclosed the leak, outed the company’s identity, and warned MobiKwik over email, the firm simultaneously took measures to stop the hacker from downloading the data.
“We […] lost access to main company servers, not surprising though…
Can’t download anything new,” the hacker said in a forum post a day later, adding that partial download might have been corrupted.
“We never wanted any money anyway, so not sad. But one of the biggest hacks of KYC ever shit!!! OR SO WE THOUGHT. 🙁 So, I guess I grow old saying I used to hack and shit. Rather than actually hacking and shit. Exciting 1 month though!!!,” the hacker said, implying that the hack dated back to January, echoing Rajaharia’s tweets from March 4.
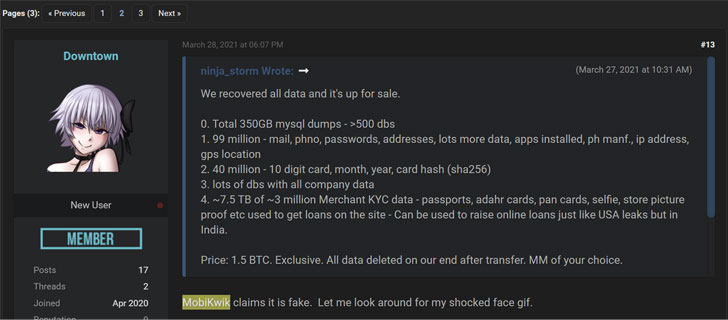
But a month later, in a separate listing on March 27, the hacker claimed, “we recovered all data and it’s up for sale,”
offering up what is alleged to be 8TB of their data for 1.5 bitcoin ($85,684.65).
However, in an interesting turn of events, plans to put the data on sale appear to have been suspended until further notice.
“Only sell this to the company after due verification that we are dealing with a company,” the hacker said in an update, implying an extortion scheme.
It’s not immediately clear how the threat actor managed to gain unauthorized access to MobiKwik’s servers, but the hacker said,
“it’ll be embarrassing for the company. story for some other time..” (sic)
The Hacker News has reached out to MobiKwik, and we will update the story if we receive a response.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter, or our LinkedIn Group.